This supplementary document is to help you
Add SSO connection in Tango portal (for admins) with your Azure Identity Provider (
IdP). You must first configure your
IdP as an admin to create an entry for Tango portal single sign-on (
SSO). Consult with your company’s
IdP expert for the latest
IdP configuration steps and instructions.
Note: This document is created in August 2024. We’re only providing a general guidance to get you started. For up-to-date procedure and screenshots, refer to the your IdP documentation.
Disclaimer: Tango has no affiliation with Azure. Tango makes no warranty of any kind, whether express or implied, with regard to any third party products, third party content, or third party services. Tango will not be liable for loss damage, cost or expense, whatsoever resulting from this guide. This guide is provided as a courtesy. To confirm accuracy or completeness of this guide, please consult with Azure directly.
To set up SSO with Azure OIDC for the Tango platform, you need an administrator account access to your IdP provider. Log in to your IdP and create and entry for the new SSO. Find out Connection display name, Client ID, and OpenID Connection ID Token Issuer URL in your IdP before continuing in Tango portal.
To set up Azure OIDC SSO:
-
Log in to Azure IdP and open Microsoft Azure Welcome page.
-
Go to Microsoft Entra ID.
-
Click Add > App registration on top, to open the registration page:
-
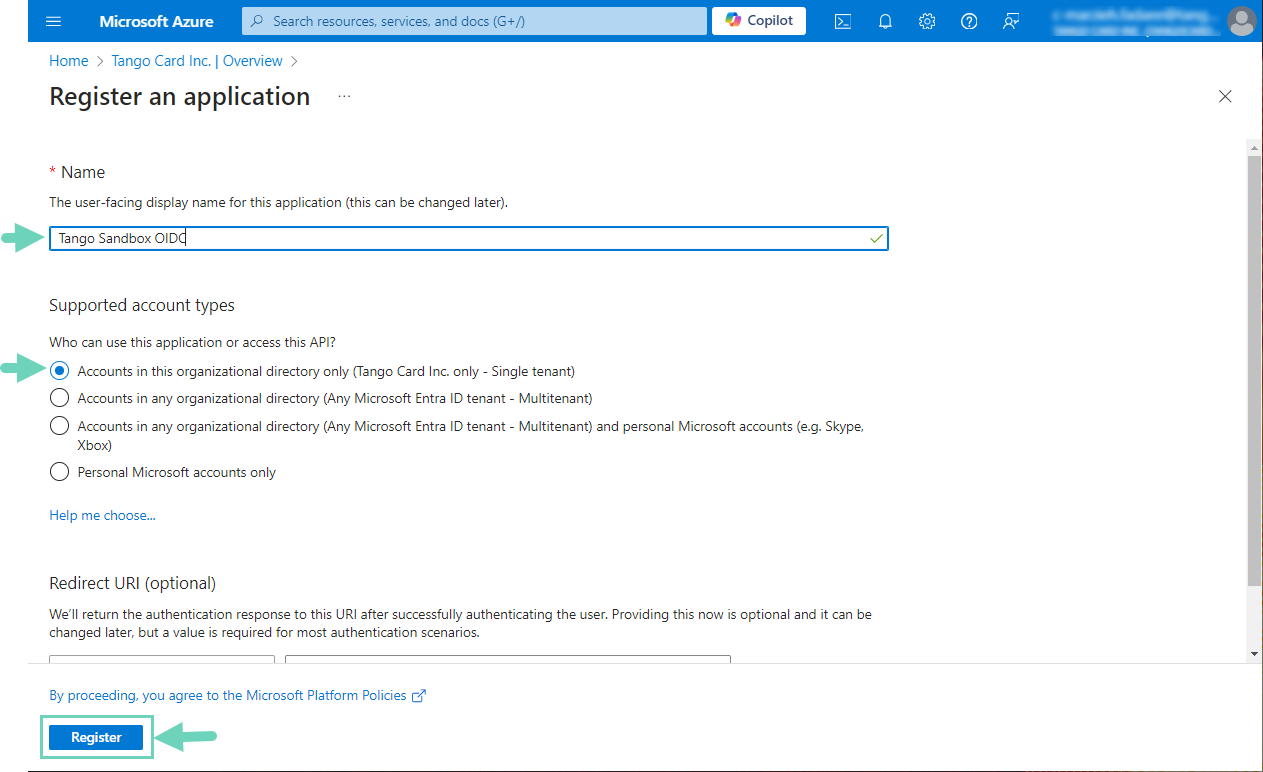
Enter a Name such as “Tango Sandbox OIDC”. The name will be shown in the the user-facing login page but can be changed later.
-
Select Accounts in this organizational directory only (default).
-
Click Register. You’ve registered an OIDC application to map to the Tango portal.
-
From the home page, search and find Enterprise applications.
-
Click the Tango application you’ve just created:
-
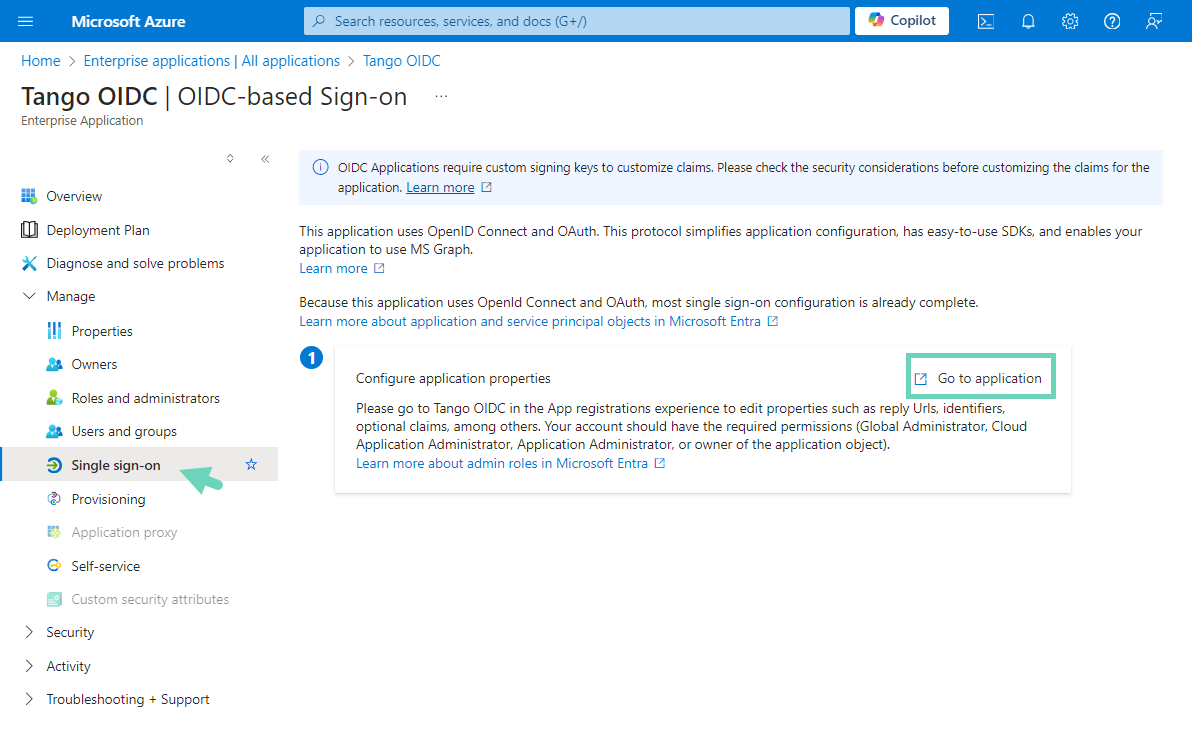
Go to Manage > Single Sign-On from the left menu.
-
Click Go to application.
-
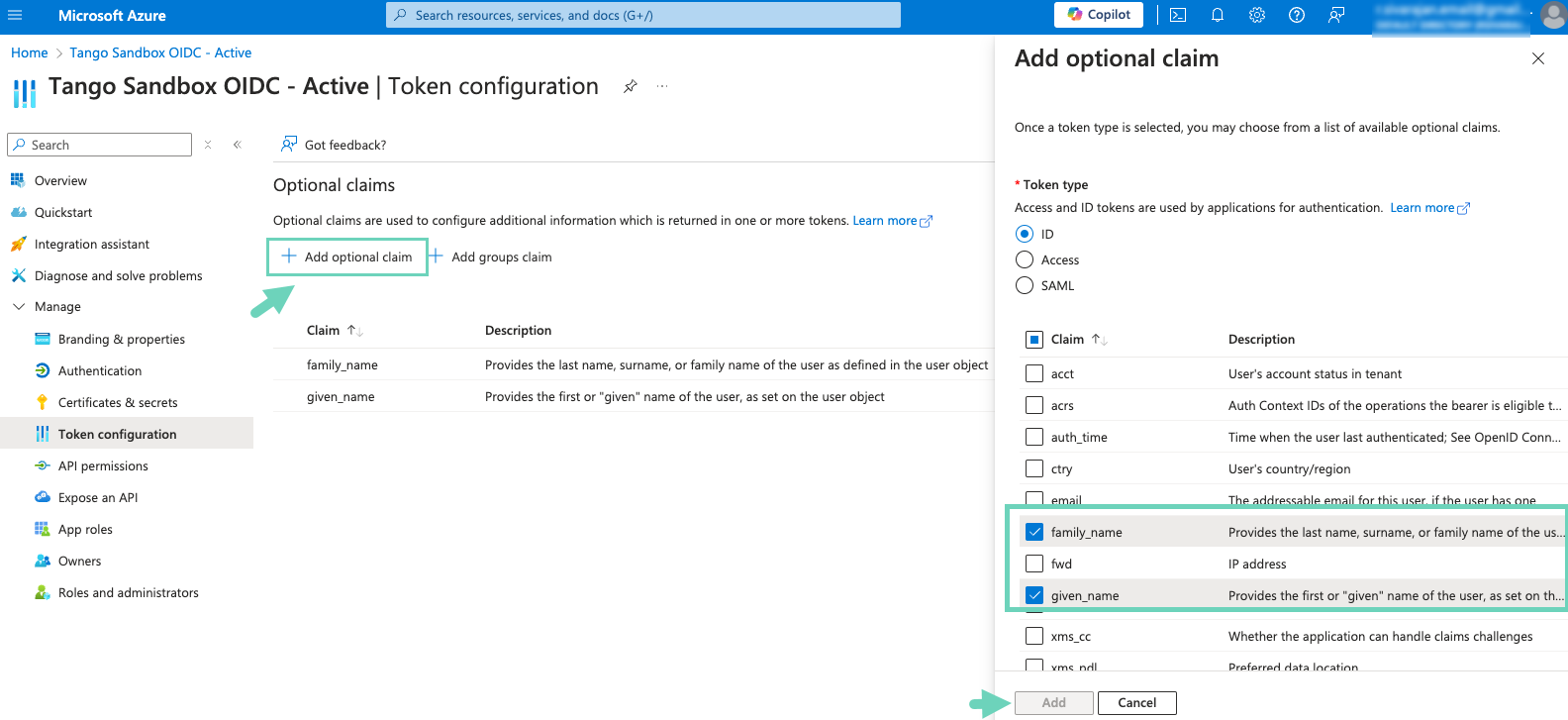
Click Manage >Token configuration on the left menu.
-
Click Add optional claim.
-
Select ID as the Token type.
-
Select family_name and given_name for Claim.
-
Click Add. The two claims will appear under Optional claims.
-
Go to Overview > Essentials:
-
Click the link next to Redirect URIs.
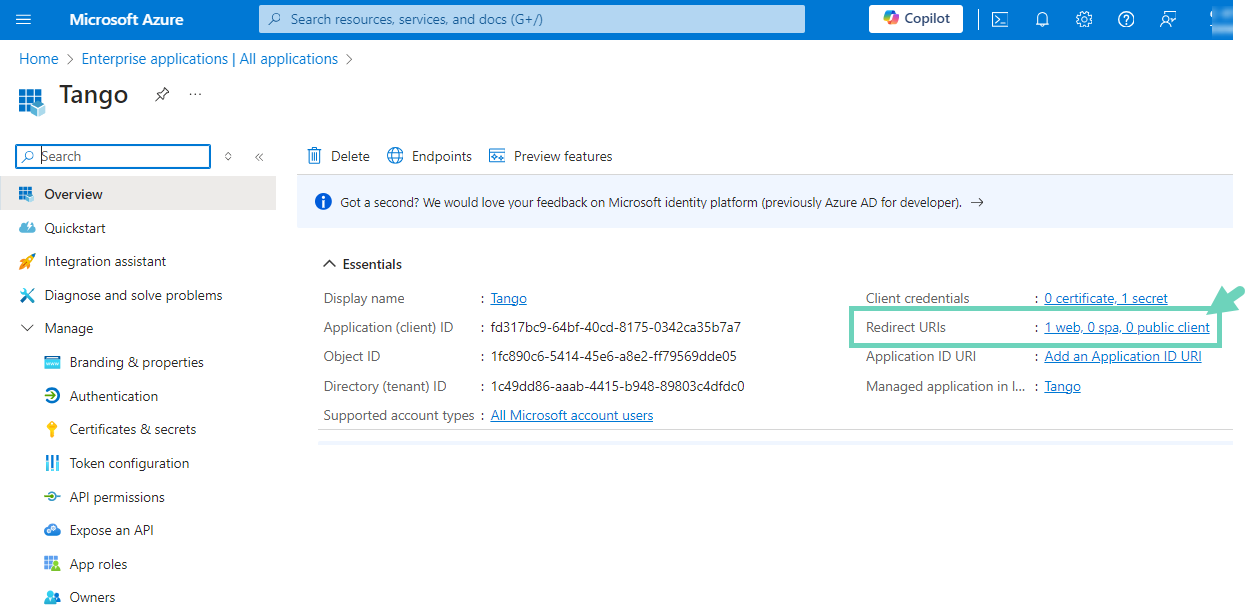
-
Click Add a platform.
-
Select Web.
-
Enter the URL you got from Tango portal:
-
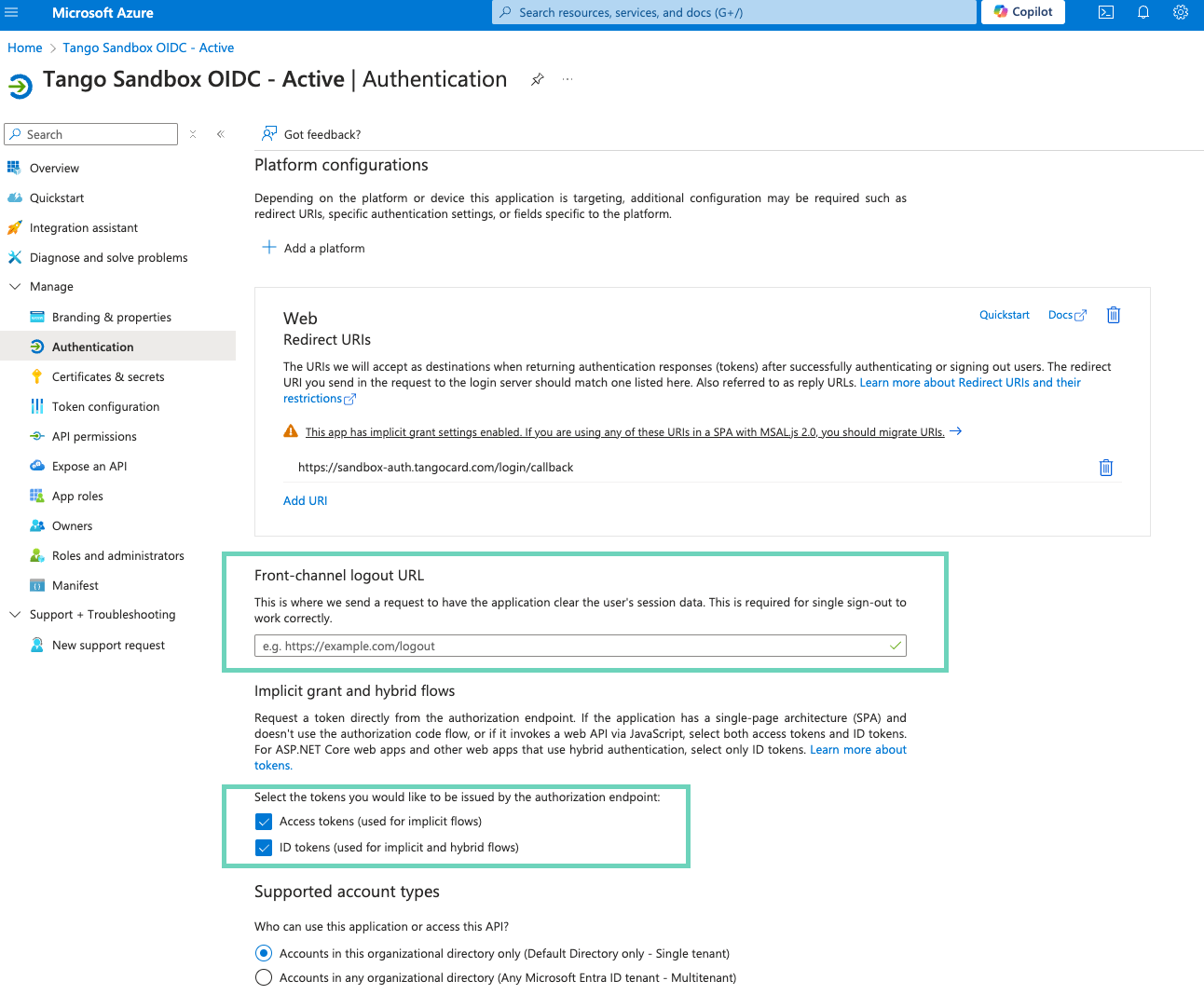
Click Configure to go to Platform configurations.
-
Select these two options:
-
Click Save
-
Go to Overview and copy the following IDs:
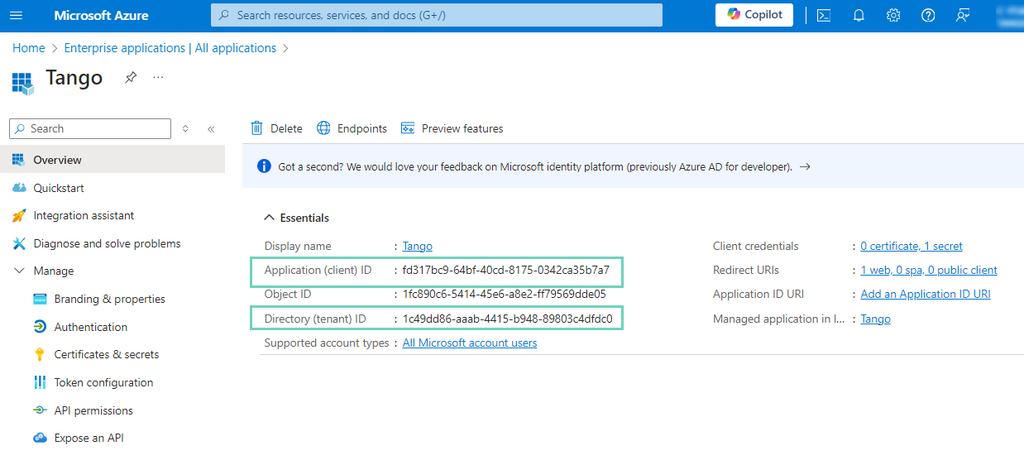
-
Application (client) ID and save it for later when configuring OIDC in Tango portal. This field will be used as Client ID in Tango portal.
-
Directory (tenant) ID and save it for later when configuring OIDC in Tango portal. This value of this field will be used as part of the OpenID Connection ID Token Issuer URL link in Tango portal.
-
Go to Overview > Essentials > Managed applications in….
-
Click Users and groups and make sure your user is included.
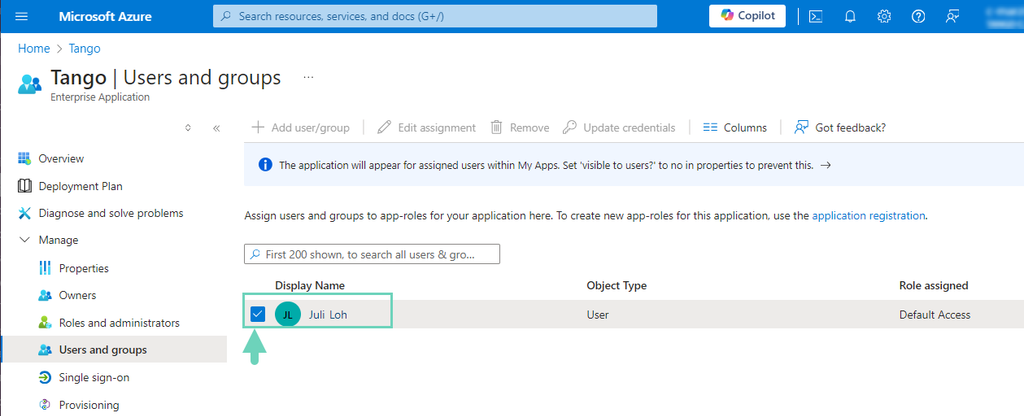
-
Sign in to the Tango portal.
-
Copy the Client ID and Tenant ID that you’ve configured here. The Tenant ID consists of three parts: Microsoft online link+ Tenant ID+ v2.0 link: https://login.microsoftonline.com/{tenantId}/v2.0/.well-known/openid-configuration.
-
Continue the SSO configuration in Tango Portal. See how to Add SSO connection in Tango portal (for admins)
To set up SSO with Azure SAML for the Tango platform, you need an administrator account access to Tango platform and the IdP provider. Log in to your IdP and create and entry for the new SSO. Find out Connection display name, Entity ID, and Metadata URL in your IdP before continuing in Tango portal.
To set up Azure SAML SSO:
-
Log in to Azure IdP and open Microsoft Azure Welcome page.
-
Go to Enterprise applications.
-
Click New application > Create your own application.
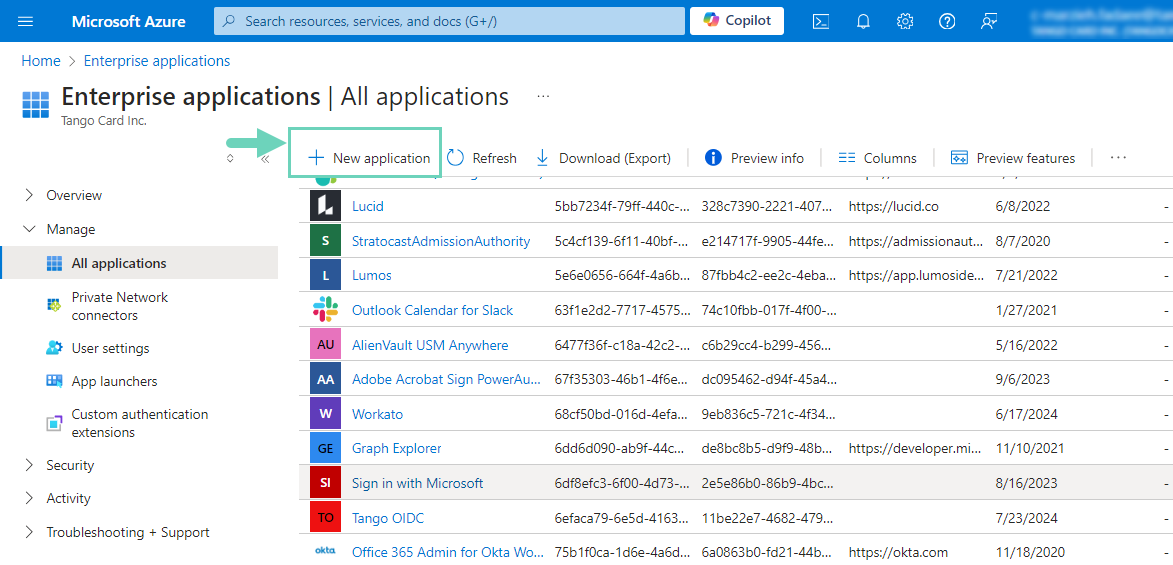
-
In What’s the name of your app, enter a name, such as “Tango Sandbox SAML”. The name will be shown in the the user-facing login page but can be changed later.
-
Click Create.

-
Go to Enterprise applications again and click the Tango application you’ve just created.
-
Go to Manage > Single Sign-On from the left menu.
-
Select SAML:
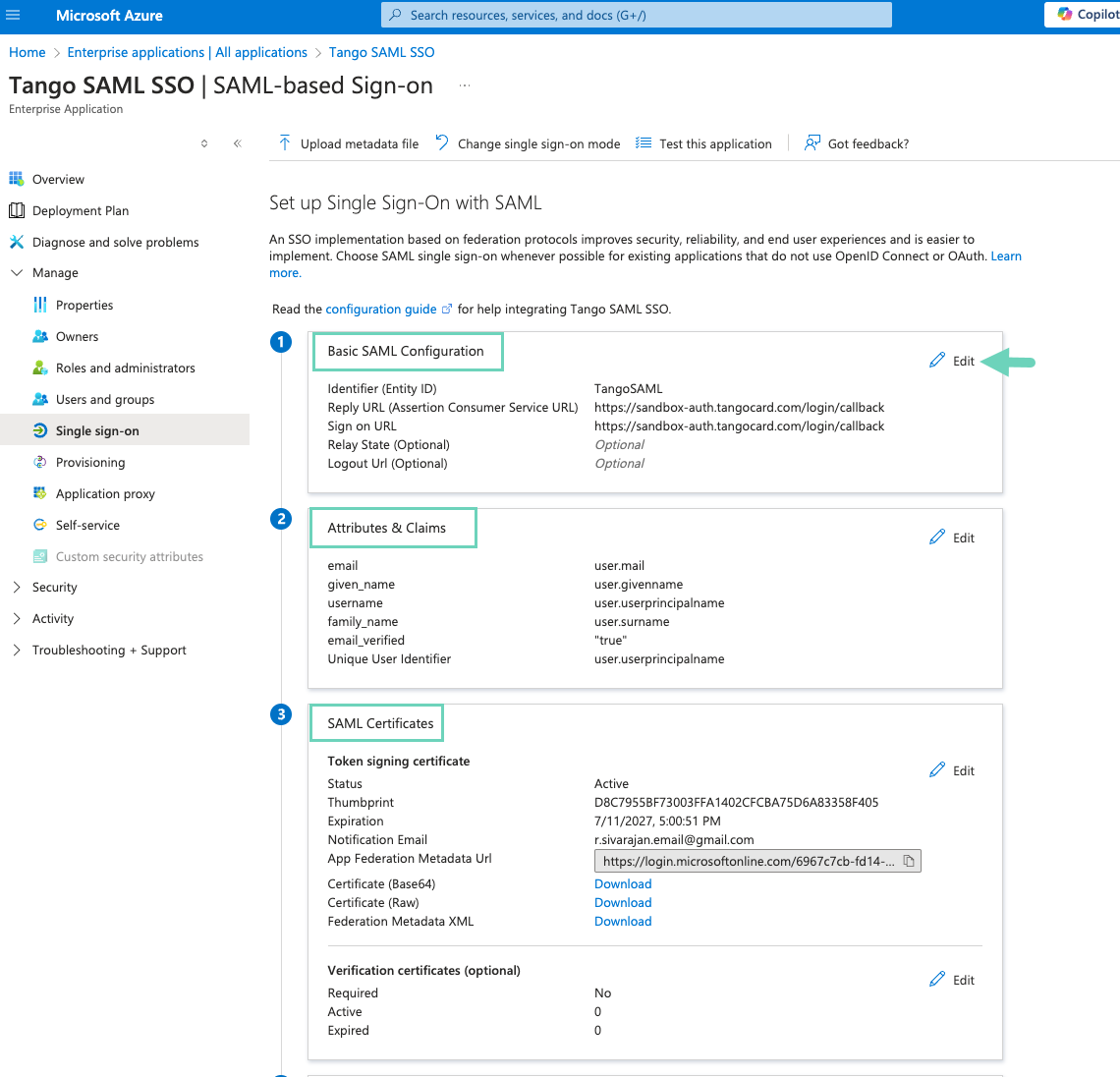
-
In Basic SAML Configuration, click Edit and enter the details such as Entity ID and Reply URL. Entity ID will be copied to Tango portal’s Entity ID field to match.
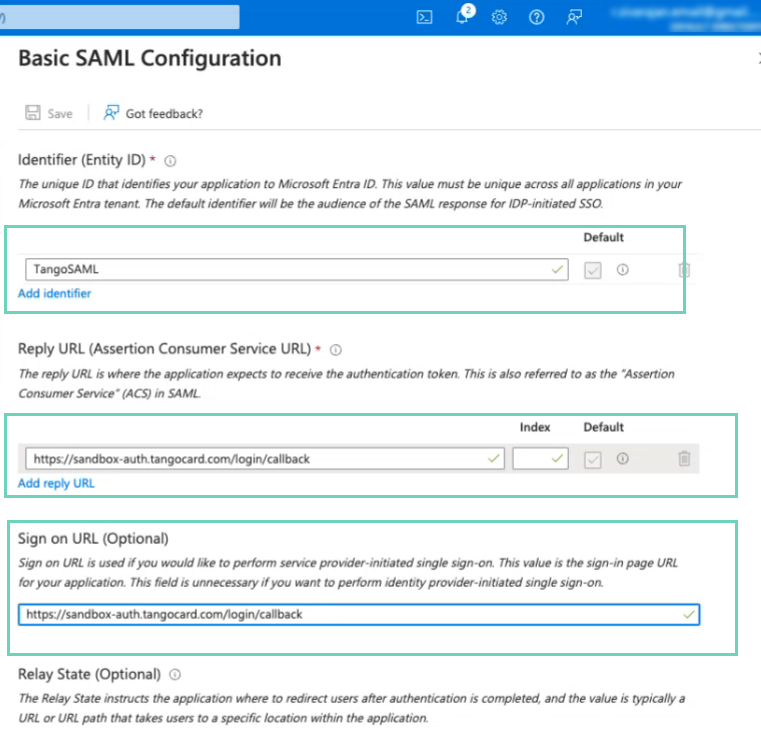
-
In Attributes and Claims, click Edit > Add new claim and enter the following attributes:
|
Attribute
|
Value
|
|---|
|
given_name
|
user.givenname
|
|
family_name
|
user.surname
|
|
email
|
user.mail
|
|
username
|
user.userprincipalname
|
|
email_verified
|
true
|
-
In SAML Certificates, click Edit and copy the App Federation Metadata URL. This metadata URL will be used later in Tango portal.
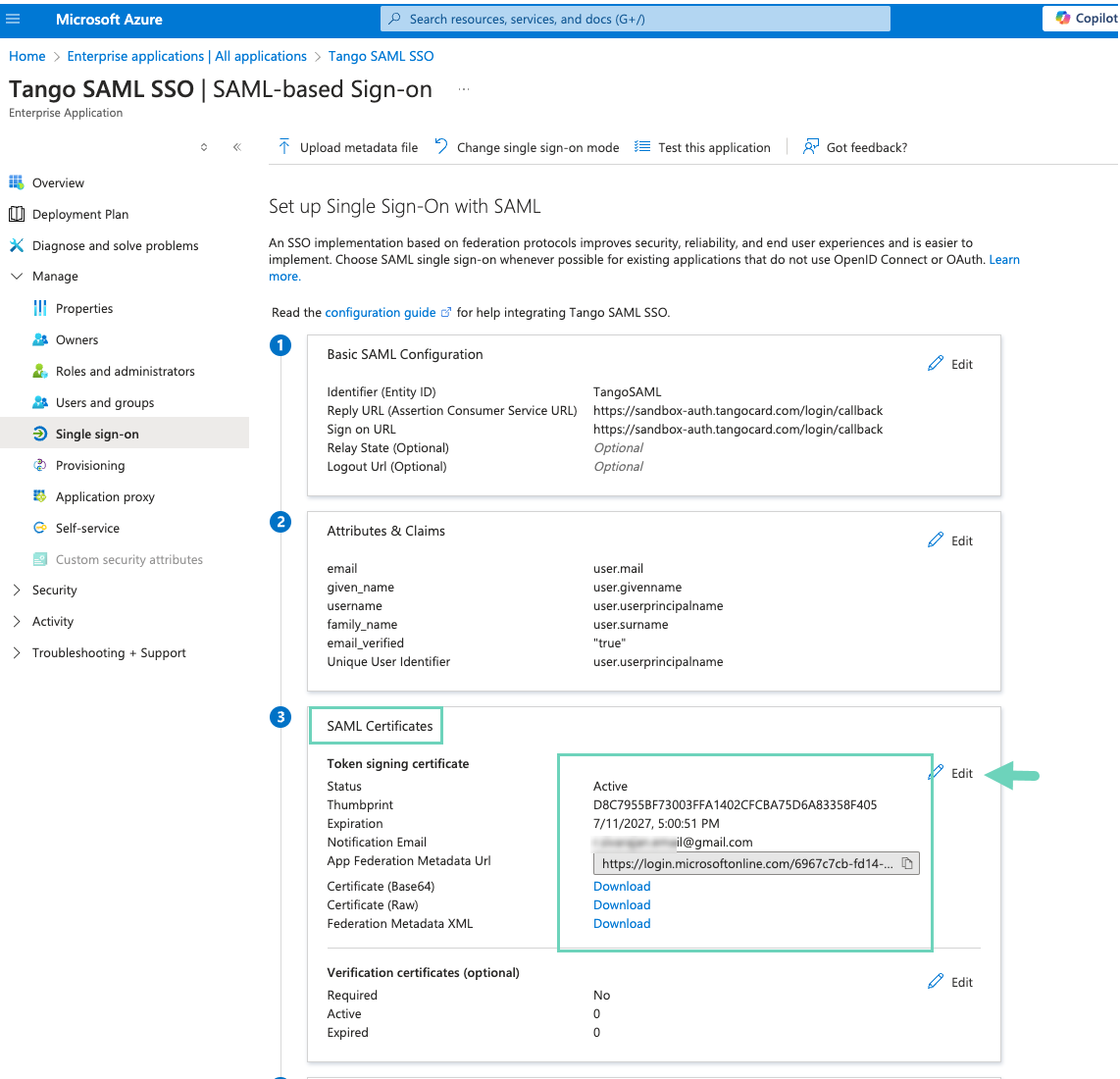
-
Click Users and groups and make sure your user is included.
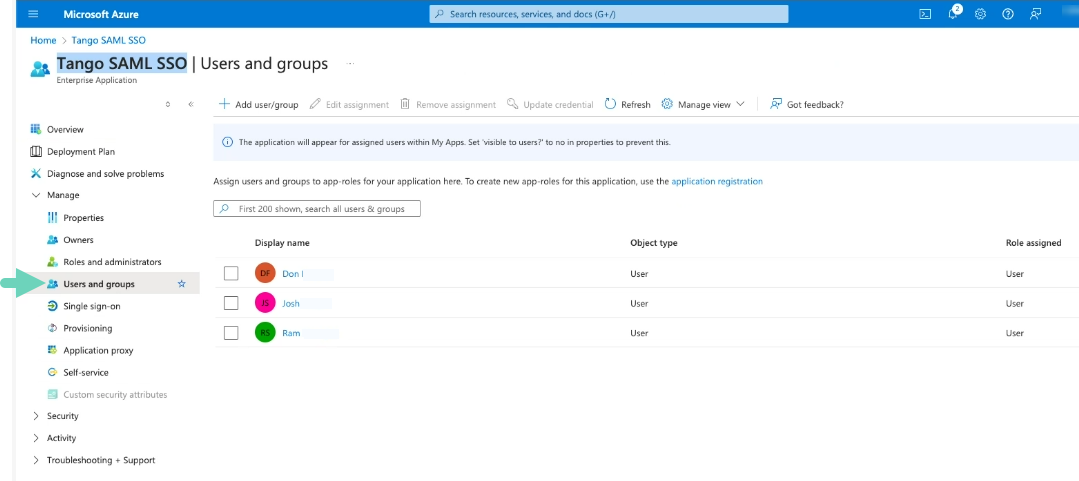
- Continue the SSO configuration in Tango Portal.
See how to Add SSO connection in Tango portal (for admins)
Add Tango SSO tile to Azure dashboard
As an IdP admin, you can add the newly created Tango SSO tile to your Azure dashboard. To start, make sure you have enabled the SSO in Tango portal. Log in to your Azure IdP and follow the instructions below:
To add Tango SSO tile to Azure dashboard:
-
Log in to Azure IdP and open Microsoft Azure Welcome page.
-
Select your Tango application (OIDC or SAML) on the list.
-
Go to Manage > Properties.
-
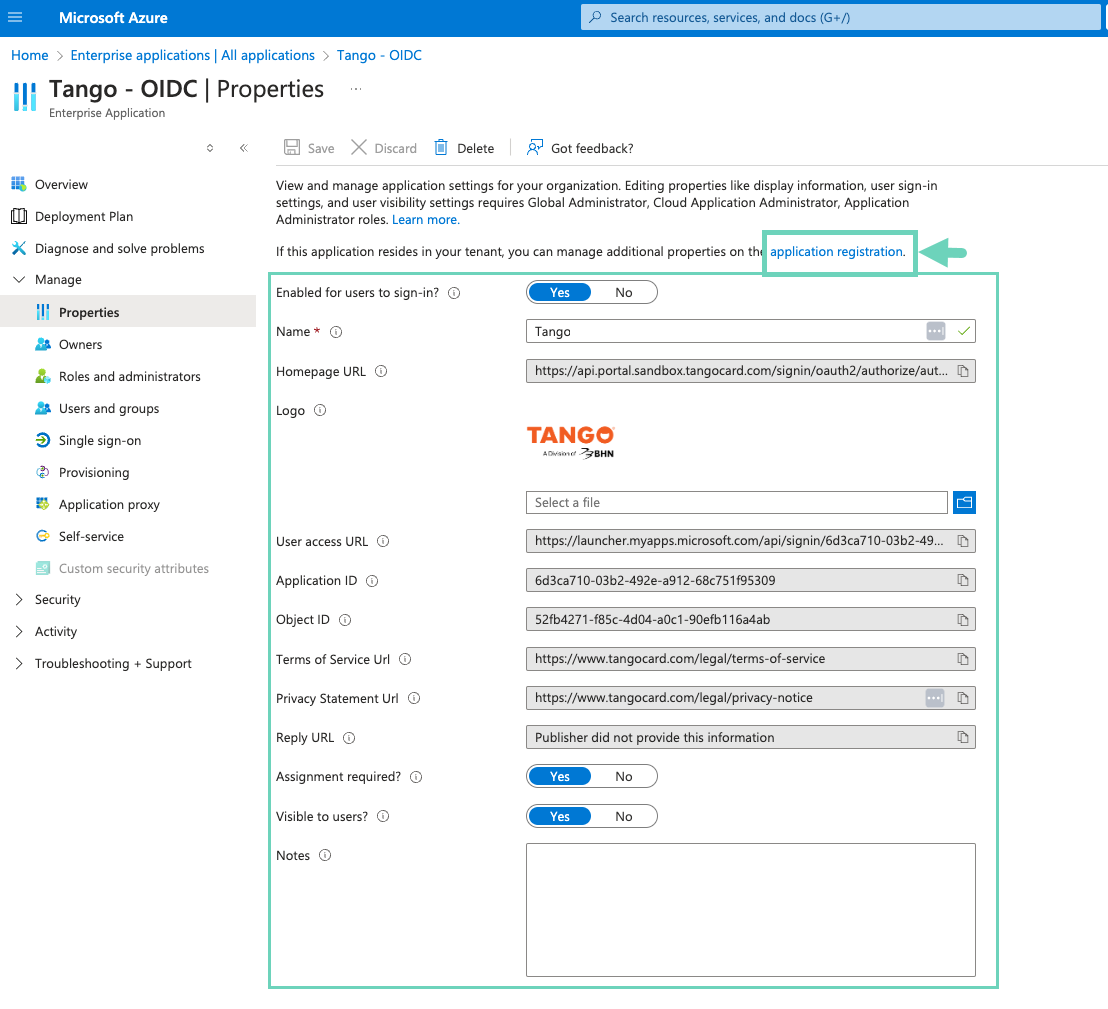
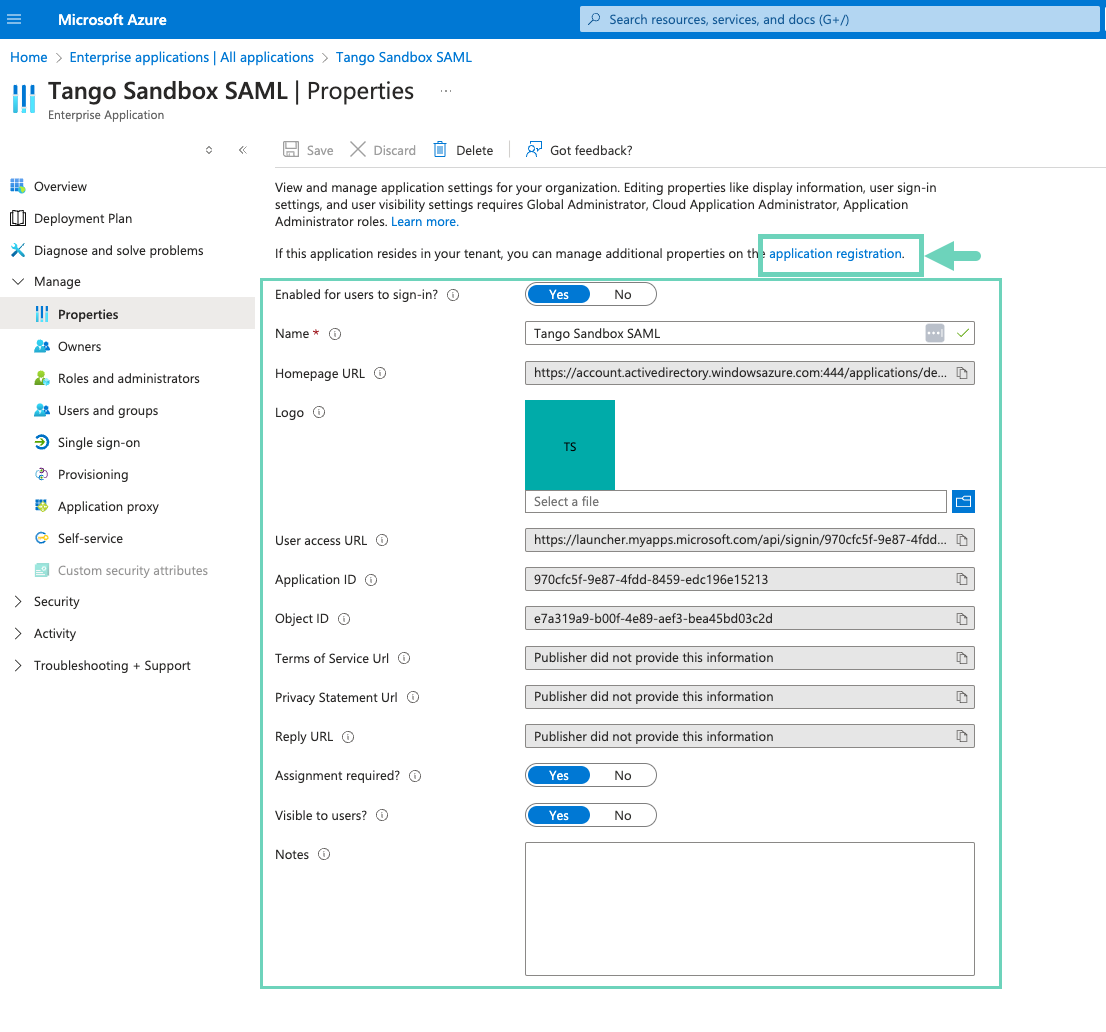
Click the application registration link on top to be able to manage additional properties.
-
For OIDC
-
For SAML
-
Enter a Name for your tile such as “Tango”. The given name will show up in your Azure dashboard later.
-
Enter the Home page URL. You must get the URL by going to Tango portal:
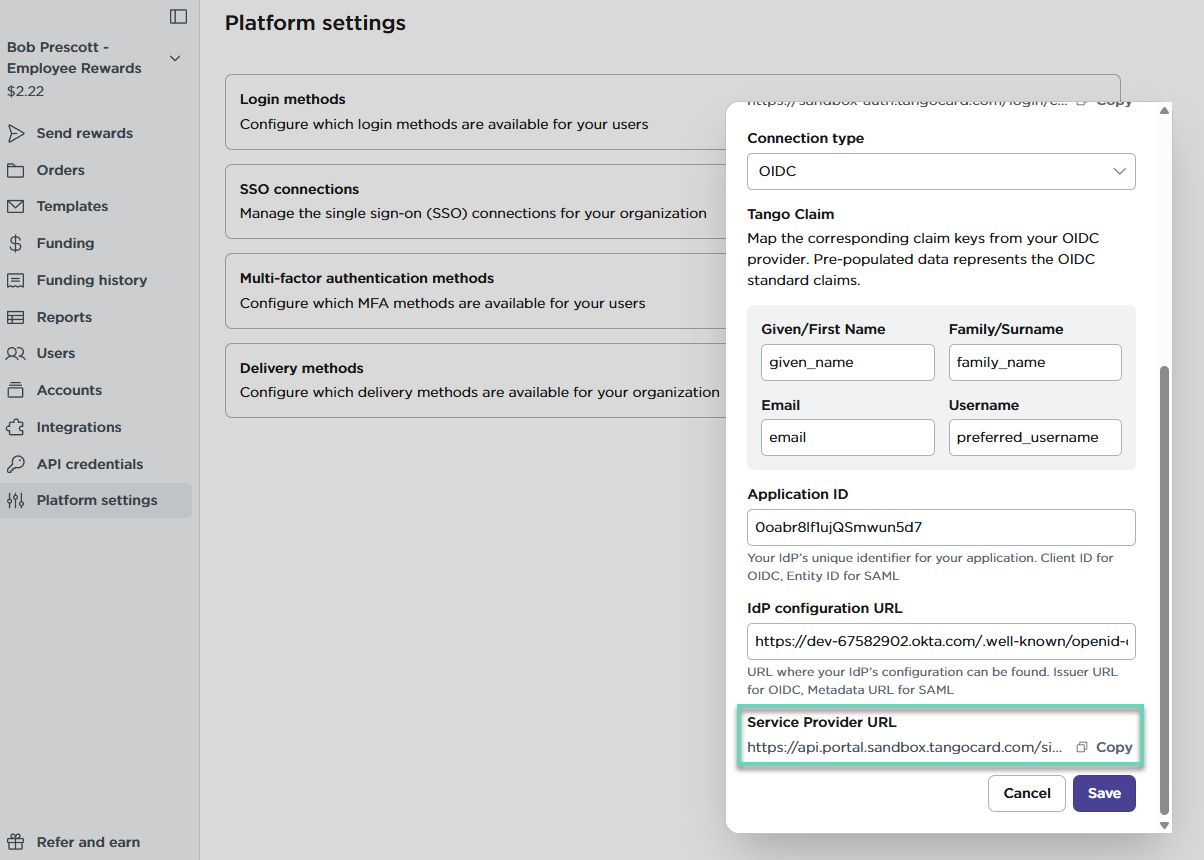
To copy the Service provider URL:
-
Sign in to the Tango portal.
-
Go to Platform settings > SSO connections.
-
Click your newly added SSO.
-
Scroll down to copy the Service provider URL and click Save. See full instructions in Add SSO connection in Tango portal.
-
Upload Tango’s Logo. Azure recommends 215 x 215 pixels for logo size:

-
(Optional) Toggle on the Assignment required to show Yes. It allows specific users to have access to SSO. If you have selected yes, assign users under Users and groups to see the SSO option when they log in.
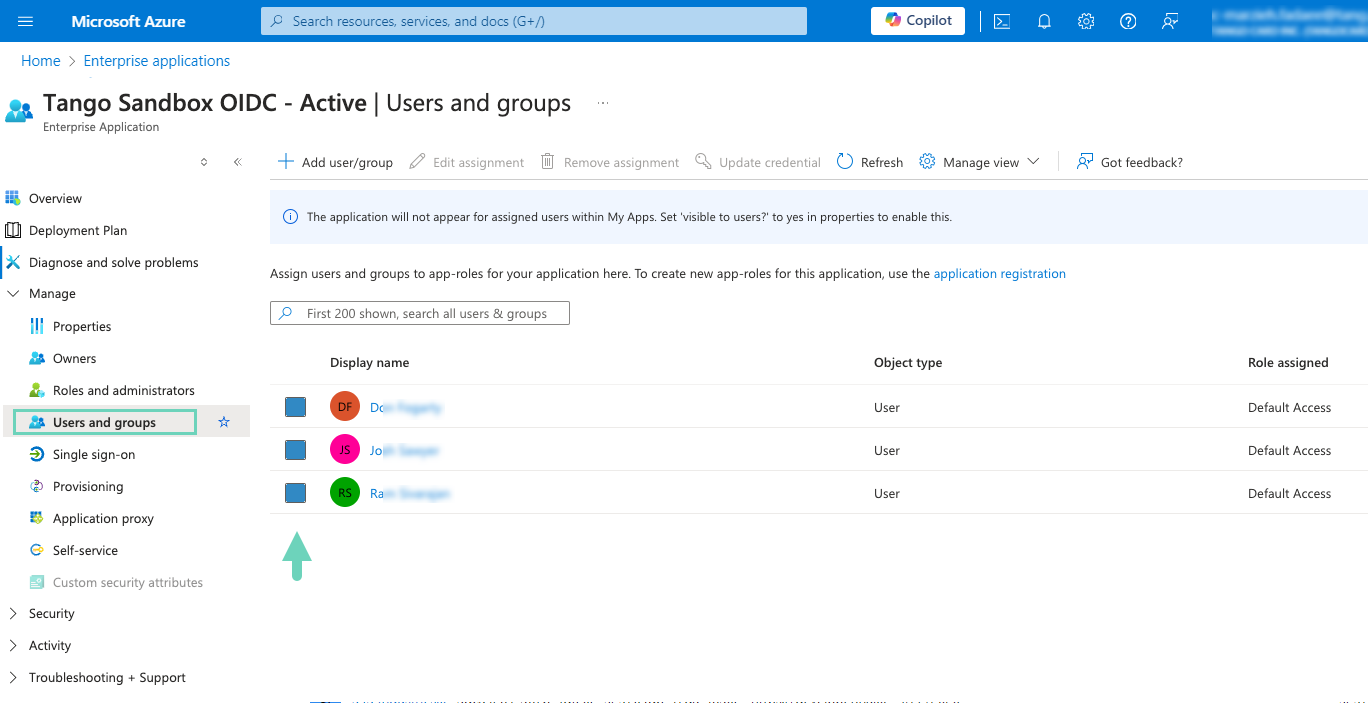
-
Toggle on Visible to users to show Yes. It allows users to see Tango SSO in their Azure dashboard.
-
Click Save.
-
Refresh your dashboard apps to see the newly created “Tango” tile.

More resources



